It is easy enough to host many sites on IIS or Apache using virtual host (or binding) on a single machine. However I have a need to run several VMs on single machine, each VM being accessible to different colleagues. Using Virtual Box (ver 5) it is easy enough to enable the Remote Desktop option, whereby you can remote desktop (eg mstsc / remote desktop app) to a VM directly.
However what was so apparent was how each VMs IIS could share a single ‘real’ world facing IP address (eg 1.2.3.4) while each VM had its own subnet (eg 10.0.2.15). The VMs could not be in the same subnet range as only 1 external IP address was available.
To achieve this goal a few things need to happen:
1) Install URL Rewrite (ver 2.0 was used) on IIS – this requires additional packages to be installed via Web Platform Installer (Application Request Routing)
2) Set up NAT on each VM virtual box setting – so that data can be sent between subnets
eg VM1 – NAT HOST port 8081 mapped to GUEST (VM) 8081
NAT HOST port 8082 mapped to GUEST (VM) 8082
VM2 – NAT HOST port 8083 mapped to GUEST (VM) 8083
3)Configure the IIS on the HOST with a new website for each website URL hosted on this server
eg website: www.testsite1.com
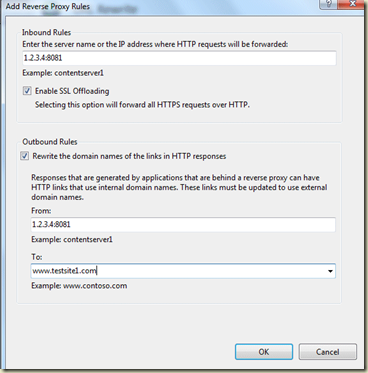
4) Create a URL Rewrite rule
For each website on the host (as created above) add a URL Rewrite rule…
The top box is the INTERNAL web address (in this case 1.2.3.4:8081)
.. and the lowest box of the 3 is the URL (eg www.testsite1.com)
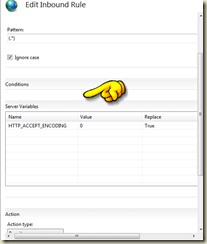
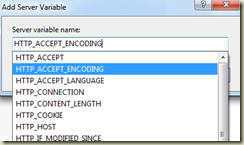
One further step (needed for gzipped compressed websites) is to add HTTP_ACCEPT_ENCODING to the Server variables. This is done in the URL_REWRITE rule (set value to 0 as GUI needs an entry).
… and then again you need to set this again from a drop down list (start typing for list to appear) of server variables.
5) Configure the IIS on the VM
The VM IIS running the website needs to be listening on the specified port (eg 8081), and not be bound to a given URL (ie binding is left blank). Also ensure the Windows Firewall on the VM is open for the port you are using (eg 8081).
Repeat using a different port for each website, and adding the details to the Firewall, Host URL Rewrite, VM NAT Port forwarding, and VM IIS website (port).